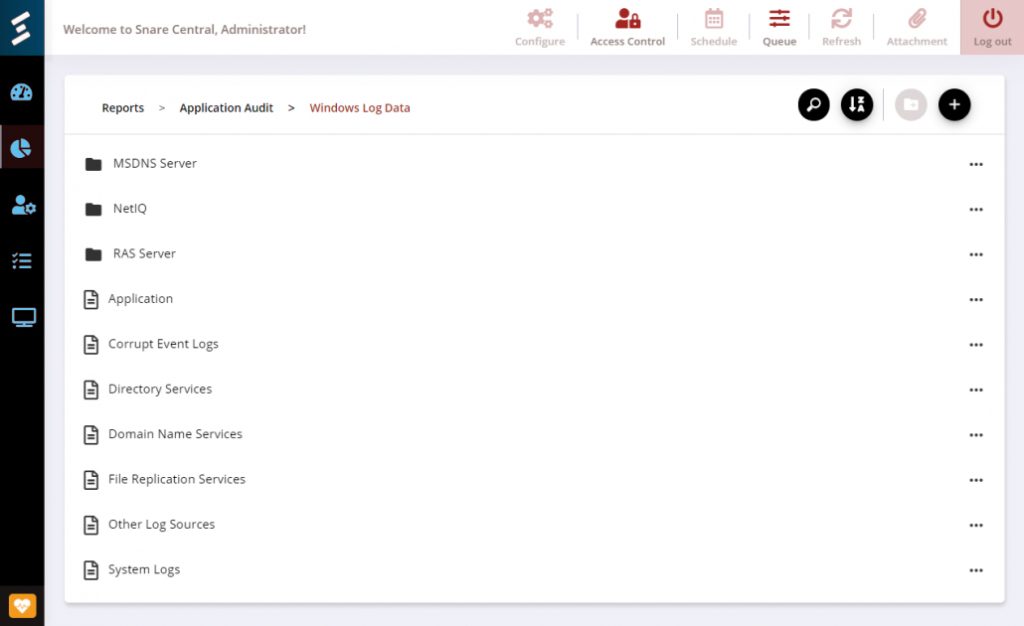
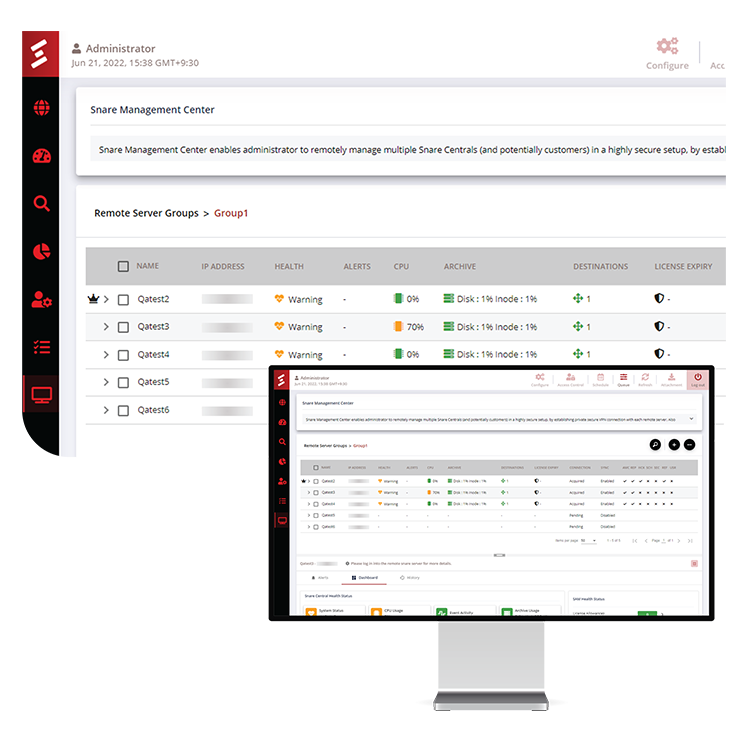
New log formats mean expanded coverage for more granular audit and forensics capability. This update will add enhanced support for Microsoft Sentinel, CEF, SQL, and Linux.
AUTOMATED ALERTING
Snare automated alerts notify your SOC or security analyst(s) immediately if there is a potential threat or anomalous activity in your system
THREAT INVESTIGATION CAPABILITIES
Snare includes FIM/FAM/RIM/RAM/USB and Database Activity Monitoring to answer critical questions in a matter of minutes: who got in, how they got in, and what they took.
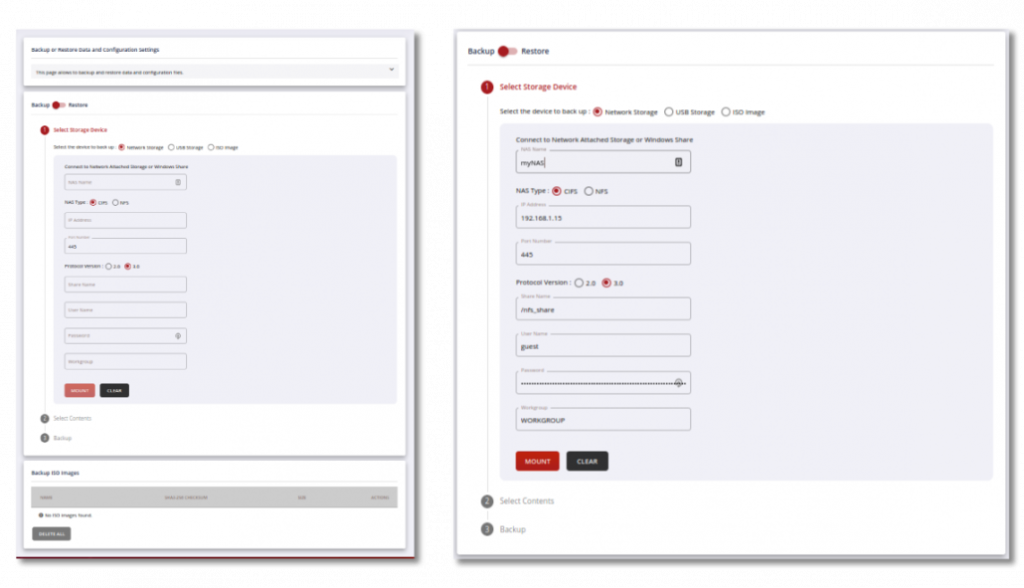
UNLIMITED, PRISTINE DATA STORAGE
Improve compliance and save money by compressing and storing an unlimited number of log data for the required timeframes in a pristine environment – logs may be required to be stored and untouched for 7+ years.
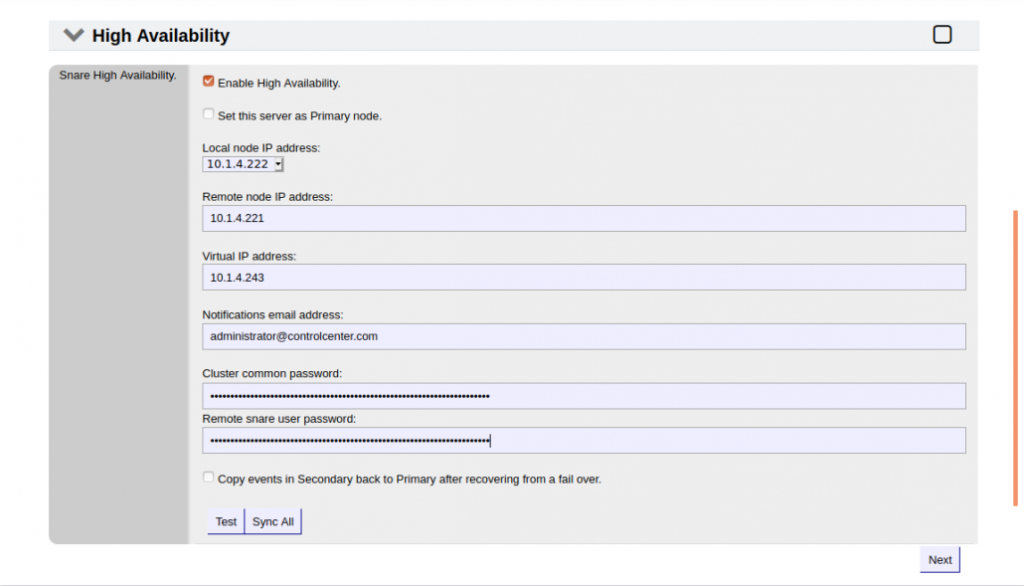
HIGH AVAILABILITY
High Availability helps to ensure there is minimal chance of lost log data, which is critical for forensic analysis in the event of a cyber attack or breach. High Availability also helps meet compliance regulatory requirements such as GDPR, ISO27001, and PCI DSS.